For digital ad campaigns to be successful, advertisers need to ensure that their ad budget is being used to reach real people. Unfortunately, with the number of different ad fraud techniques on the rise, this is more difficult than ever.
One common technique that is particularly worrisome for advertisers is domain spoofing ad fraud. That’s why in this article, we’ll explore the different types of domain spoofing techniques, their threats, and how you can detect and prevent them from damaging your ad campaigns.
What is domain spoofing ad fraud?
Domain spoofing is a technique widely used in online advertising. Malicious actors use this technique to mask unsafe websites by actively hiding, tampering with, or mismatching the domain where the traffic originates from. The main objective of domain spoofing is to hide real website domains from users. On a surface level, these domains or URLs look reputable and legitimate.
This type of ad fraud is usually enacted by low-quality publishers attempting to disguise themselves as premium publishers within advertising marketplaces for several reasons:
- To sell expensive traffic
- To hide the origin of the traffic if the website has illegal or undesired content
- To avoid conflict with brands that are “particular” about the sites their ads are placed
- To run phishing schemes
Often, they do this by building a domain name that very closely resembles the URL of a legitimate publisher and displaying a duplicate copy of the real website’s content.
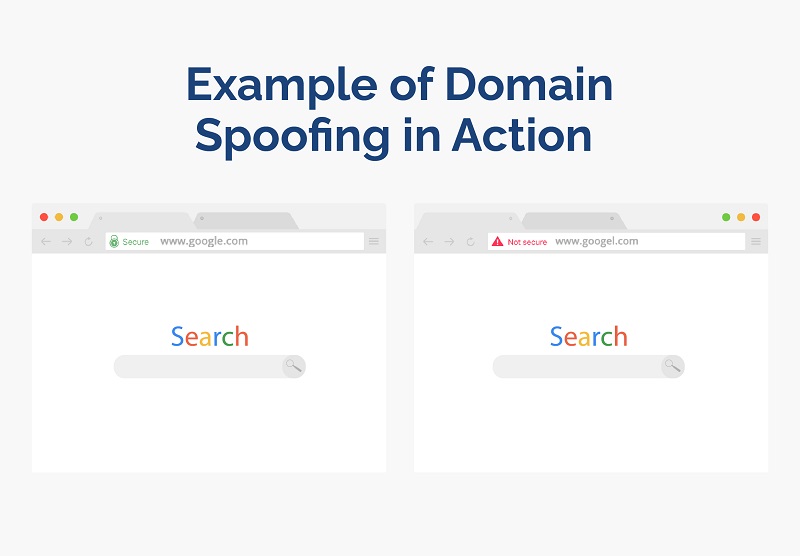 The two websites look virtually the same, but the URLs in the address bar show that only the left page is the original while the right one is the fraudulent page.
The two websites look virtually the same, but the URLs in the address bar show that only the left page is the original while the right one is the fraudulent page.
This results in advertisers believing that their ads are being displayed on premium websites with the correct target audience. However, by employing domain spoofing, fraudsters display them on low-quality sites.
One of the most notable examples of domain spoofing ad fraud is the Methbot scheme, which was able to spoof over 6,000 premium publishers and generate up to $5 million in fraudulent ad revenue per day.
4 Types of domain spoofing
Domain spoofing types can be divided between simple methods and those that are more complex and sophisticated.
Basic domain spoofing methods involve creating web domains that closely resemble other websites, while more complex methods usually involve either infected or fraudulent websites, or malware or infected browsers. This includes websites that load iFrames inside premium, legitimate websites in order to generate large amounts of premium traffic and malicious browser extensions that can load extra ads in pages and modify search results.
Let’s take a closer look at both simple and sophisticated methods of domain spoofing ad fraud.
URL substitution
As the name suggests, URL substitution occurs when fraudsters replace and imitate URLs in order to trick advertisers into placing an ad on an illegitimate website instead of a premium one.
This method is basic since fraudsters need only build a website with a URL that closely resembles an original URL — usually ones that advertisers trust. They’ll also imitate the website’s content, layout, and images to fool unwitting advertisers.
Sometimes, fraudsters will simply misspell a word or add extra characters within the URL in the hope that users won’t notice. Other times, they’ll use Unicode characters (a universal character encoding standard) that look almost identical to regular characters.
Cross-domain embedding
Cross-domain embedding is another basic domain spoofing tactic but involves more input on behalf of fraudsters.
First, fraudsters identify one website with high traffic and low-quality ad inventory (adult websites, “fake news” websites, etc) and another with low traffic and high-quality ad inventory. Then, they’ll impose nesting iFrames, containing ad-sized versions of the low-quality website. Put simply, by embedding low-quality websites or ads within iFrames, the ads appear as if they’re being shown on the high-quality website, and fraudsters receive the views from the nested iFrames.
Anti-fraud solutions can help mitigate cross-domain embedding as it identifies iFrames and we collect all domains, including the current iFrame domain and the parent domain.
Custom browsers
Custom browsers are created so that bots can visit any website on the internet, while appearing as if “users” are visiting from a premium website, simply by copying the header information from these premium websites. The header information sent by the browser is therefore spoofed, while fraudsters capitalize on ad budgets. Anti-fraud solutions can identify custom browsers based on behavior and missing features.
Malware
Using infected apps or browser extensions (that are usually accompanied by click spamming), fraudsters can inject ads into websites and apps without user knowledge. Malware is usually identifiable by random pop-ups from websites and website redirects. The clicks that are generated by malware produce payouts for fraudsters. Anti-fraud solutions can help mitigate malware by checking information such as windows and sizes and background usage.
What are the common indicators of domain spoofing attacks?
Many domain spoofing attacks can be identified by the naked eye. For example, a quick examination of a URL can often reveal an extra character or a misplaced character.
Other types of domain spoofing attacks can be identified with analytics tools. For instance, if users want to check that the traffic coming from a real-time bidding feed is truly from a certain domain, they can check the real domain names in their analytics back end.
Users can also check the amount and quality of traffic that they’re receiving, as well as the cost-per-mille (CPM). However, a fraud detection tool, such as Opticks, is the best way of gaining visibility into all of this data and making sense of it in order to protect your ad campaigns.
How to prevent domain spoofing from damaging your ad campaigns
Domain spoofing can drain ad budgets quickly, which makes preventing it a high priority for your organization. Here, we explore the ways you can stop fraudsters from using domain spoofing methods to bleed your budgets dry.
Manual checks
Domain spoofing discrepancies are often noticeable once you take a closer look, and so completing regular manual checks can help you identify domain spoofing quickly. However, with so many different types of ad fraud to be on the lookout for, coupled with high volume ad campaigns, manual checks can become cumbersome and time-consuming.
Use ads.txt
The Interactive Advertising Bureau (IAB) developed ads.txt — a list file of authorized ad vendors — in an attempt to curb domain spoofing ad fraud. Ads.txt, which stands for ‘Authorized Digital Sellers’, was created to be a free and easy way for publishers to list the authorized entities who sell their ad inventory. Publishers simply add a text file containing a list of the approved vendors to their site.
While the number of publishers incorporating ads.txt into their sites is growing, fraudsters are aware of this prevention technique and can evade detection by exploiting other loopholes. This means that ads.txt cannot prevent 100% of domain spoofing attempts.
Invest in a dedicated anti-fraud solution
Manual checks and ads.txt can only take you so far in the fight against domain spoofing. When we consider attacks like cross-domain embedding, for example, these prevention methods will fall short since ads are first served to quality, safe websites, and then appear on unsafe websites.
Fortunately, anti-fraud solutions can identify when browsers have been spoofed, and can also pinpoint whether browsers match the devices being used, which is critical for identifying non-human browsers.
At Opticks, we protect your organization from complex domain spoofing attacks with our proprietary algorithms and custom telemetry to make sure you’re not falling victim to the effects of domain spoofing ad fraud.
Here’s the reality: being a victim of domain spoofing can have long-lasting, damaging impacts on your brand and ad campaigns, and depleted budgets and a loss of user trust are just the beginning.
We’ve shown you how fraudsters carry out domain spoofing attacks and how to spot them — but now it’s time for you to protect your organization. To learn more about how the expert team at Opticks can help defend your ad spend, contact our team here for a free demo or start your free trial.
