Android smartphone users have unrestricted access to around three million apps listed on Google’s Play Store. To the average user, all of these apps appear legitimate and safe to install for use on their devices. However, a dark side of the Play Store does exist — and, as of yet, it’s an issue that hasn’t been fully examined.
In fact, Google’s Play Store was found to be the primary source of malware installs on Android devices, with the study estimating that somewhere between 10% and 24% of the listed apps could be labeled as malicious or unwanted. Many of these will be attributed to fraudsters using fake app package names to masquerade as legitimate apps.
Here, we go through what fake app package names are, some examples, and finally, how fraudsters are able to fake app package names.
What are fake app package names?
All Android apps have a package name attached to them that uniquely identifies the app on devices and in the Google Play store. Once an app is published, the package name cannot be changed.
Fake app package names are essentially “repackaged apps” that are used by fraudsters to distribute malware across smartphones. They are able to masquerade as official and legitimate apps, and display as almost mirror-images of the user interfaces users are accustomed to using. In effect, these fraudsters hide in plain sight.
Since the infected apps still function as usual, the malware is difficult to detect to the naked eye. It’s incredibly easy for users to be unaware of when they are downloading malicious and rogue applications onto their smartphones.
Photo editing apps and games are common targets for fraudsters faking app package names, with many users unaware of the malware since the apps work exactly as they are expected to.
How do fraudsters fake app package names?
The act of faking app package names is incredibly easy for fraudsters to carry out. Looking at anti-fraud activities that detect malicious traffic, it’s very common to see legitimate apps on top of malware.
When a mobile application makes a request to a web resource — for example, a landing page — the app is expected to identify itself by adding its package name to the request.
In order to do this, apps use the HTTP header X-Requested-With command, such as “X-Requested-With com.facebook.katana”. This header, as with all headers, is very easy to spoof or tamper with via automated actions and bad bots. In essence, a malicious actor can claim to be a legitimate app with minimal effort.
How do fake app package names work in action?
There are multiple instances where Google has discovered fraudulent apps and subsequently removed them. Many of these apps have four and five-star ratings on Google’s Play Store and on the surface, appear to be completely safe. At Opticks, we are often ahead of the curve and are able to block fraudulent apps even before they appear on Google’s radar.
To demonstrate how easy it is for fraudsters to spoof application names, below is an example of real Java source code used by fraudsters inside an Android app:
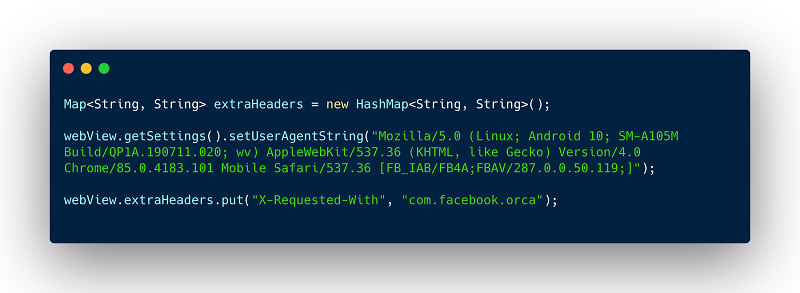 Java source code used by fraudsters inside an Android app
Java source code used by fraudsters inside an Android app
Fraudsters have it just as easy when using automated tools such as bots. With a few lines of JavaScript code they can tamper with the headers and remain undetected without further protective measures.
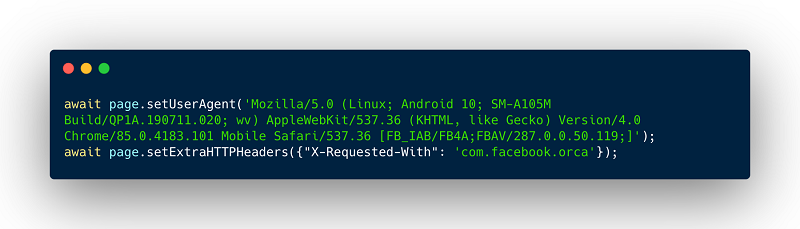 JavaScript source code used by fraudsters using a headless browser (puppeteer)
JavaScript source code used by fraudsters using a headless browser (puppeteer)
What threats do fake app package names pose?
Overall, the threats caused by fake app package names are very similar to the threats caused by other widespread instances of ad fraud — chiefly, depleted budgets, skewed metrics, and customer and client dissatisfaction. Malicious code can also steal personal and financial information from the user.
However, the users that this type of fraud generally pretends to be also tend to be more expensive — for example, Facebook and Instagram users — since in traffic acquisition, users coming from social media or other high-quality apps are more costly than sites with a bad reputation, such as streaming sites. Even low quantities of these “users” is usually more costly. Since the traffic that comes from these users also appears to be of higher quality, the fraud becomes harder to detect.
Detect fraudsters’ fake app package names with an anti-fraud solution
Although Google has expanded its Play Protect security system to protect users against harmful app behavior — a system that uses machine learning to scan apps and analyze their risk — many apps with fake package names are still falling through the cracks.
Opticks uses machine learning to detect and block fraudsters attempting to spoof app package names, in turn, protecting your in-app ads. To learn more about how we can work together to prevent attacks on your ad spend, click here to contact us and request a free demo or start your free trial.
