Fraudsters are well versed in mimicking real user behavior to bypass checks and balances. They’re also experts in identifying organizations’ advertising weak spots and exploiting them for financial gain.
Just like there are good bots and bad bots, there’s good proxy traffic and bad proxy traffic. Unfortunately, fraudsters often give proxy web traffic a bad name.
Real online users often use proxies to protect their identity or evade location-based rules associated with streaming services in different countries. By using proxies, only the IP of the proxy service they’re using, not their device’s IP address can be seen. Fraudsters, on the other hand, use proxies to circumvent fraud detection rules and carry out malicious actions.
In this article, we will explore the different types of proxy traffic, how fraudsters use it, the threats it can carry, and how advertisers can prevent it.
What is proxy traffic?
A proxy, which has its own IP address, acts as an intermediary between one computer and other servers. Proxies are frequently used for security purposes, including filtering harmful traffic, intercepting malware, and hiding users’ locations.
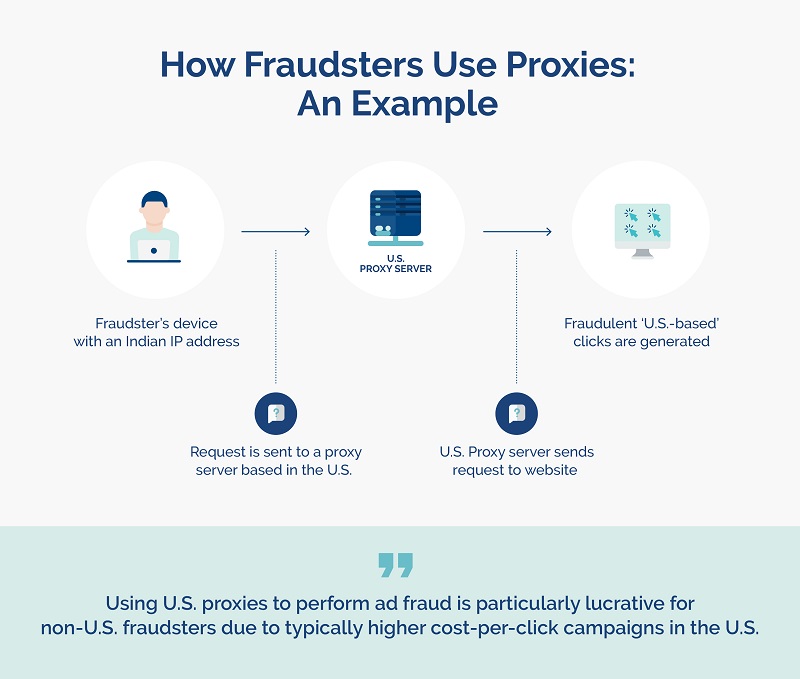
Although these are legitimate reasons for using a proxy, they’re also an incredibly attractive vehicle for fraudsters to use since they can hide their real locations behind multiple proxy IP addresses. In many cases, fraudsters use proxies to commit click fraud by rapidly changing their IP addresses and clicking on ads over and over again.
Proxies can be categorized in three groups:
- Web and public proxies: These make connection requests on a user’s behalf. Public proxy server software can be configured by the administrator to listen to a specified port. Proxies are used for several reasons, including filtering web content, avoiding restrictions such as parental blocks, screening downloads, and providing anonymity.
- Virtual Private Network (VPN) proxies: These services are used to route all network traffic through them, usually encrypting and securing all network traffic. While this is a common practice for companies or institutions to allow connections to their internal networks, VPN traffic also comes from Tor exit nodes or anonymizer VPNs.
- Hosting/Content Delivery Network (CDN) proxies: These include hosting providers, data centers, and Content Delivery Network IP addresses.
What makes proxy traffic attractive to fraudsters?
Public proxies, hosting providers, and VPNs are all popular vehicles for bad actors to perform fraudulent activities. Proxy traffic is appealing to fraudsters for several reasons:
- They provide anonymity: Proxies allow fraudsters to hide their location, servers, and networks. This can enable them to access the content they would likely be blocked from viewing, or to evade location-based fraud detection methods.
- They allow fraudsters to access higher PPC campaigns: Certain regions, such as the U.S., typically offer higher financial rewards on PPC campaigns. Fraudsters use proxies to bypass the location rules on ad campaigns.
- They enable faster navigation: Since data centers and hosting providers operate powerful networks, fraudsters use these proxies to accelerate the speed at which they can carry out fraudulent activity.
- They can use residential proxies: Fraudsters can purchase and use residential proxies to browse the internet from a certain country or via a certain carrier. This often happens without the knowledge of the IP address’ real owner.
What are the threats posed by proxy traffic?
Using servers preloaded with VPNs, fraudsters commonly use click farms and botnets to send flurries of fraudulent clicks to ad campaigns from anywhere in the world — resulting in wasted impressions and drained campaign budgets.
More sophisticated bots might even use expensive residential proxies to fake their location and/or network. For instance, they can make it appear as if they’re browsing with a mobile 4G connection from a certain country and carrier.
For advertisers, proxy traffic is also problematic from a technical point of view. Since proxies either prevent advertisers from viewing locations, or provide them with false proxy locations, advertisers are unable to optimize campaigns based on location and language.
Plus, proxy traffic also affects browser fingerprinting. Advertisers are unable to access user information, such as whether they are new or returning users.
How to detect proxy traffic and protect your campaigns
Traffic surges from unusual locations — especially those outside of your campaign’s target zone — can be a telltale sign of fraudsters using proxy traffic to target your ad campaigns with click fraud.
Once large peaks in traffic have been identified, many organizations take to their server’s logs with a fine-tooth comb to weed out suspicious IP addresses in order to manually put them on a blacklist. However, even when using a tracking script to identify fraudsters, this is an incredibly time-consuming task.
Since proxies are so useful for fraudsters, organizations must take action in preventing them from affecting their campaigns.
Opticks’ proxy detection system uses several internal and external sources to construct a proxy database with more than a million IPs, which is updated daily. Combined with our proprietary fraud-detection algorithms, organizations can rest easy knowing their campaigns are protected against harmful proxy traffic.
Find out more about how the expert team at Opticks can help protect your advertising campaigns by booking a free product demo or starting your free trial.
