What is Clickjacking and How Can it Affect Your Campaigns?

 By
Eduardo Aznar
·
3 minute read
By
Eduardo Aznar
·
3 minute read
All types of ad fraud have similar consequences: wasted ad budgets, skewed campaign data, and reputational damage, to name a few.
However, although various ad fraud methods -- such as ad stacking and pixel stuffing -- affect organizations in comparable ways, how they are carried out differs. This means that it’s incredibly important for organizations to be aware of not only the dangers of each type of ad fraud but also how fraudsters exploit vulnerabilities in the first place.
Clickjacking is an extremely common type of ad fraud whereby users’ genuine clicks are redirected to the fraudsters’ destination of choice, with the intent of carrying out malicious actions.
To help you understand why preventing clickjacking is so important, we’ll explore how it works, the threats it poses to your organization, and the solutions you must implement to prevent it.
What is clickjacking and how does it work?
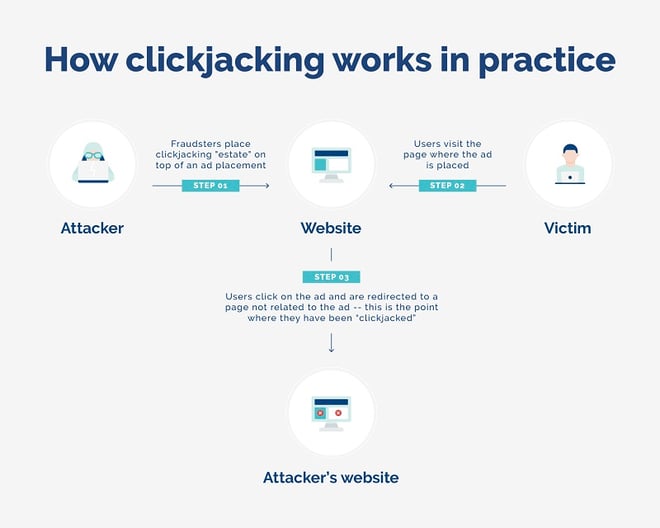
Clickjacking, also known as “User Interface (UI) redress attack” is a clever portmanteau of the words “click” and “hijacking”, and it occurs when fraudsters trick users into unintentionally clicking a webpage element.
Fraudsters do this by overlaying hidden malicious content over a trusted page or HTML element of a webpage inside a 1x1 iFrame. When users click on a seemingly innocent item on the page, they are taken to the fraudsters’ desired location instead of the location indicated on the webpage. Users’ clicks, therefore, are used to trigger a malicious action.
Common malicious actions triggered by clickjacking include tricking users into:
- Downloading malware
- Visiting unsafe websites
- Giving away personal credentials
- Authorizing transfers of money
- Activating cameras and microphones.
Clickjacking is also used as a common ad fraud technique, by redirecting clicks on online ads and stealing the earned commission.
What are the threats posed by clickjacking?
Clickjacking is routinely carried out via apps and mobile web pages since it’s easier to produce fake clicks there. Let’s take a look at some of the damage that can be caused by clickjacking practices.
Wasted ad budgets
Like most forms of ad fraud, clickjacking has the potential to drain ad budgets quickly and efficiently. Since users’ clicks are redirected to clicks on online ads that are not intentional, organizations are charged for clicks that don’t convert and bear no value.
Skewed campaign data
Since clickjacking represents clicks that aren’t genuine and provide no value, campaign data becomes skewed and often useless when it comes to informing future campaigns.
Compromised equipment
When users are tricked into clicking a webpage element, this can sometimes trigger the download of malware onto their device. Performing virus scans, reinstalling operating systems, and device reformatting can soon become a costly affair.
Clickjacking can also authorize control of device features such as enabling microphones and cameras.
What can you do to identify and prevent clickjacking?

Clickjacking can be difficult to identify since many of the elements used are hidden or invisible. However, there are some common markers that may point to your organization being a victim of clickjacking:
- High bounce rates
- Repetitive IP addresses
- Traffic from unusual sources and/or locations.
There are different ways of preventing clickjacking from harming your organization’s bottom line -- client-side and server-side methods. Let’s take a look at both preventative approaches.
Client-side methods
The most common client-side method of clickjacking mitigation is called framebusting, which prevents a site from functioning when loaded inside a frame. This method does not require modifications to be made to HTTP headers, only to the webpage’s HTML code.
Client-side methods can be effective at preventing clickjacking attacks, but they can also be easily circumvented.
Server-side methods
“X-Frame-Options” is an HTTP security header that ensures that no content from your website can be embedded onto another website. However, the X-Frame-Options header is very limited, since it is not supported by all browsers.
Content Security Policy (CSP) frame-ancestors can also be used in the same way, but again, are not supported by all major browsers yet.
Use an anti-fraud solution
Using an anti-fraud solution is the best way to prevent clickjacking. It allows you to easily monitor and proactively block suspicious activity before it becomes a problem for your site and systems.
Defend your organization against clickjacking
Preventing clickjacking attacks cannot be done manually in an efficient manner. Not only is it a tedious process, but it wastes precious time and resources that you could be expending on growing your business and ensuring successful ad campaigns.
If you suspect or are certain that you’ve become a victim of clickjacking practices, it’s time to take action. Anti-fraud solution Opticks uses advanced machine-learning algorithms to detect and prevent clickjacking before it has a chance to drain your budgets.
To learn more about how the expert team at Opticks can help protect your organization against clickjacking, contact our team here for a free demo.
