What Are MSISDN Injections and How to Prevent Them

 By
Marc Rubia Criado
·
2 minute read
By
Marc Rubia Criado
·
2 minute read
There are multiple types of ad fraud that are common knowledge across the industry; clickjacking, ad stacking, pixel stuffing, and botnets, just to name a few.
However, there are other ad fraud techniques that are lesser-known that have the potential to drain budgets rapidly. MSISDN (Mobile Station International Subscriber Directory Number, more commonly known as a phone number) injections are one type of online fraud that those in the industry are less familiar with, and less likely to be equipped with the tools to be able to prevent it.
MSISDN injection is a very prevalent fraud technique in the Telecom and Direct Carrier Billing industries. It aims to defraud end-users (subscribers to telecom) by subscribing them to products and services without their consent through their operator billing systems.
To help you understand why preventing MSISDN injections is essential, we’ll explore how fraudsters enact them, the threats they pose to your organization, and the solutions needed to help curb their damage.
What is an MSISDN injection and how does it work?
MSISDN injection is a header enrichment process used to add the MSISDN (phone number) to the browser's headers, in order to automatically identify the user and their payment details through their SIM (subscriber identification module) card or mobile bill.
MSISDN header enrichment is a technology from the WAP era that is still used by carriers worldwide and is usually restricted to some IP address blocks.
This MSISDN header should only be available after the user has gone through the carrier or partner’s WAP internal gateway and is inside the carrier platform while using mobile data.
Fraudsters inject random, stolen, or fake MSISDN values while browsing to either access easier flows (for example, to skip the SMS code verification process) or to trick the carrier (an MSISDN added by the carrier's billing process). Then, when the billing process is executed, the carrier will either discover that the MSISDN does not exist, or will receive complaints from affected users.
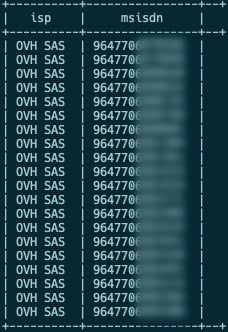
Example of MSISDN injected in traffic coming from an online virtual hosting internet service providers
Due to the private nature of this data and how the enrichment system works, MSISDN headers cannot be present outside the carrier's internal platform. Therefore, it’s clear MSISDN injection has occurred when they appear on a public landing page, on redirect chains, or any other place that is not within the carrier's internal platform.
Put simply, fraudsters “inject” MSISDN into HTTP (Hypertext Transfer Protocol) headers. The discovery of MSISDN information in browser headers is a clear indication of online fraud.
What are the threats posed by MSISDN injections?
MSISDN injection aims to defraud end-users (telecom subscribers) by subscribing them to products and services without their consent. As a result, end-users are charged for things they didn’t sign up for, while operators will receive customer complaints and, in turn, see a deterioration of their Net Promoter Score (NPS) and customer churn.
What can you do to prevent MSISDN injections?
MSISDN injections can only be effectively prevented using a sophisticated anti-fraud solution to verify that users are not browsing with MSISDN-related headers outside the scope they are available (carrier's internal platform).
Anti-fraud solution Opticks has a specialized solution for Direct Carrier Billing. We also have a list of MSISDN headers used by carriers all around the world, plus mechanisms to detect whether users are browsing with these headers, among other advanced techniques to analyze whether the presence of these headers makes sense in the context that they exist.
To find out more about how the expert team at Opticks can help protect your organization against MSISDN injections, contact our team here for a free demo.
