Ad Fraud Techniques 101: The Complete Guide to Ad Fraud

 By
Eduardo Aznar
·
10 minute read
By
Eduardo Aznar
·
10 minute read
How many types of ad fraud techniques are you aware of? Of those that you know of, can you explain how each works, and how they threaten your organization?
Being able to fight ad fraud demands an understanding of the types of techniques fraudsters use day in, day out. In this article, we go through fourteen of the most common types of ad fraud techniques, how they work, what threats they pose, and tips for preventing them from becoming a threat to your organization.
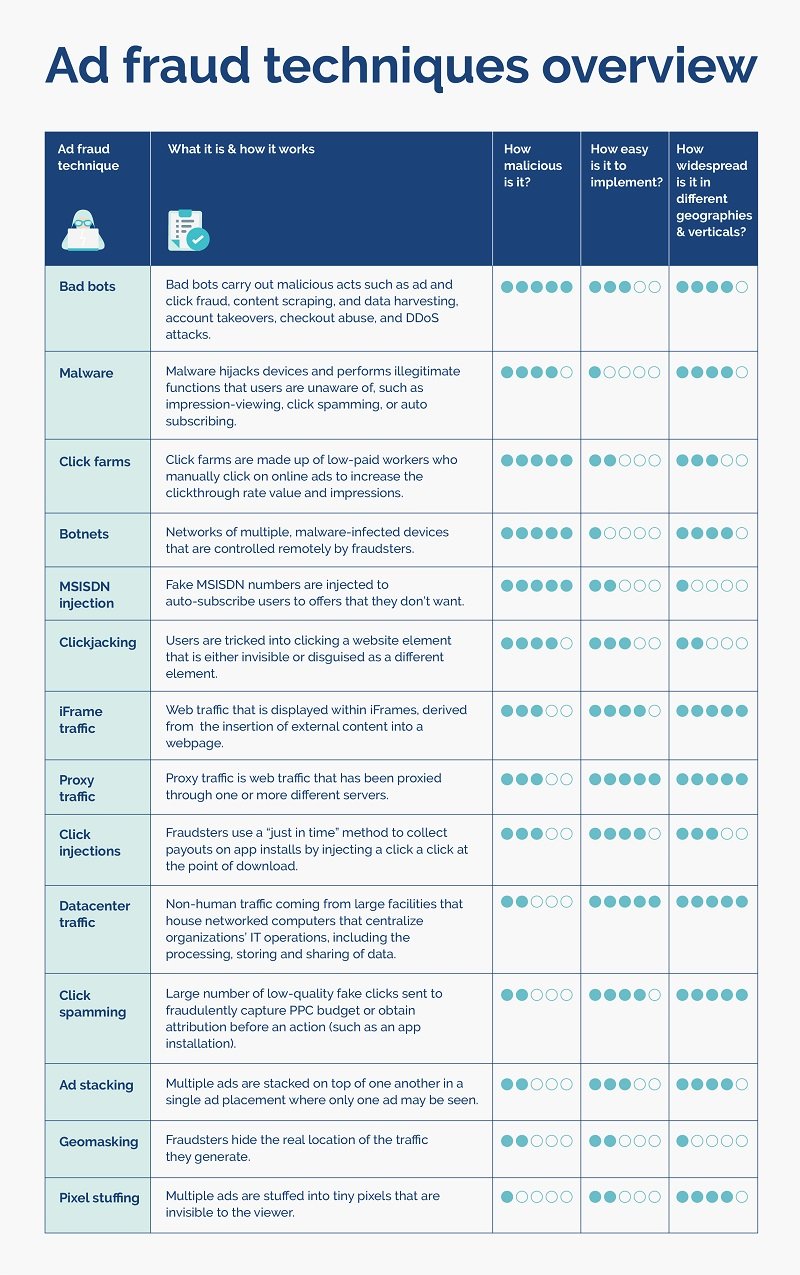
14 Ad fraud techniques and how to prevent them
Not only is the occurrence of ad fraud on the rise, but so too are the ways it’s carried out. Below, we go through how each ad fraud technique works, the risks they pose to your organization, and how to prevent them from damaging your ad campaigns.
Index
- Ad stacking
- Bad bots
- Botnets
- Click farms
- Click injections
- Clickjacking
- Click spamming
- Datacenter traffic
- Geomasking
- iFrame traffic
- Malware
- MSISDN injection
- Pixel stuffing
- Proxy traffic
Bad bots
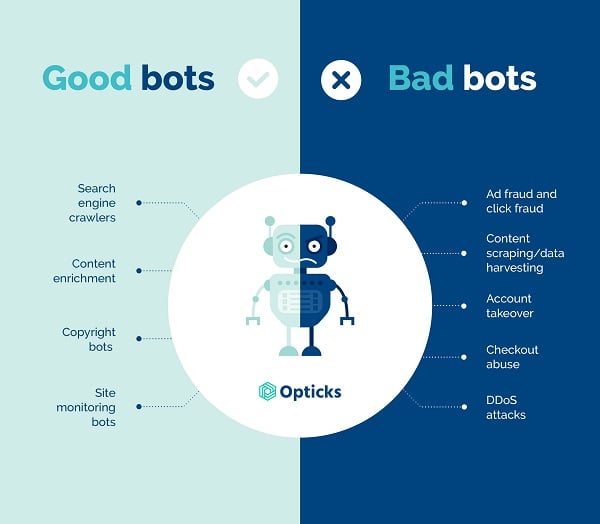
What are bad bots?
Bad bots are bots that carry out malicious acts such as ad and click fraud, fake clicks, fake impressions. Other actions include content scraping, data harvesting, account takeovers, checkout abuse, and DDoS attacks.
How do bad bots work?
Bad bots are constantly maturing and evolving into more sophisticated threats. They’re progressively able to emulate real human workflows across web applications to appear as real users. Bots make it seem like an ad is receiving a ton of impressions, yet it’s simply being scanned by a bot.
What are the threats posed by bad bots?
Bad bots are extremely malicious. They can generate a huge number of fake clicks to completely drain ad budgets quickly and from afar. They contribute to impression fraud, click fraud, lead fraud, subscription fraud, attribution fraud, and skewed analytics
They can also swiftly serve malware to users, steal data and credentials, plagiarize content, and siphon thousands of dollars from your budget.
Related techniques: Datacenter traffic and proxy traffic.
Malware
What is malware?
Malware hijacks devices to perform illegitimate functions that users are unaware of. This occurs when fraudsters sneak malicious code into installations.
How does malware work?
Unaware users install fraudulent apps/software development kits (SDKs), which load ad impressions outside of the user’s visible area of a webpage. The app or SDK will then fraudulently trigger clicks or perform lead generation activities. Apps outside of the Google Playstore are an important vehicle of this ad fraud technique.
Users may realize that their devices have become hijacked by malware when they notice an increase in data usage, battery drainage, and unwanted subscriptions through their carrier billing.
What are the threats posed by malware?
Malware hijacks devices to perform impression fraud, click fraud, lead fraud, subscription fraud, attribution fraud, and can also skew data and analytics.
Malware can also waste media budgets by creating fake clicks and impressions. It can also skew engagement metrics and incorrectly influence future ad spending decisions.
Related techniques: Bad bots, click spamming, pixel stuffing, ad stacking, click injection, MSISDN injection, and geomasking.
Click farms
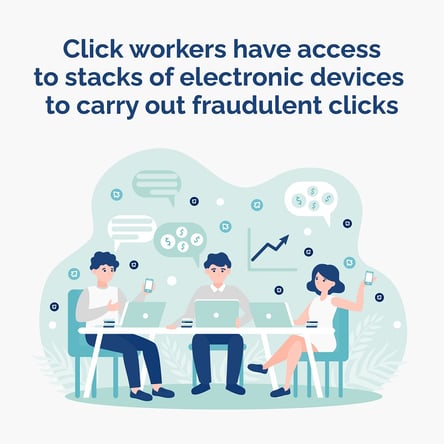
What are click farms?
Click farms (and lead farms) are made up of low-paid workers who manually click on online ads in order to increase the clickthrough rate value and impressions.
Farms can also become lead farms when they are used to carry out lead generation fraud. Humans fill out forms with randomized information (or belonging to real people, without their knowledge or consent).
How do click farms work?
Click farms vary in sophistication, but the concept is simple. Imagine a large room filled with people sitting in front of computers and/or phones. They sit there manually clicking on ads in order to drain ad budgets.
What are the threats posed by click farms?
A click farm’s main aim is to drain ad budgets, and it’s done in a relatively easy way. They are used to carry out impression fraud, click fraud, lead fraud, subscription fraud, attribution fraud, and can skew data and analytics.
Plus, click farm operations are usually based in countries where there is little regulation against this type of fraudulent activity, such as China, India, and the Philippines, making it even more difficult to hold them to account.
Related techniques: Geomasking and click spamming,
Botnets

What are botnets?
Botnets are a network of multiple, malware-infected devices that are controlled remotely by fraudsters to carry out malicious activities such as marketing fraud, credential leaks, DDoS attacks, and data theft.
A botnet’s objective is to infect as many connected devices as possible and use them for automated, repetitive tasks that users cannot detect.
How do botnets work?
Botnets use infected devices to partially override web browsers to divert fraudulent traffic to click on online ads. By using only a small fraction of web browsers, they’re able to remain invisible to the user.
What are the threats posed by botnets?
Botnets are highly malicious. The number of fake clicks they can generate can completely drain ad budgets in a very short amount of time and can do so from afar. In totality, they can be used to carry out impression fraud, click fraud, subscription fraud, and attribution fraud. Botnets also lead to skewed analytics, and can also break through passwords and security questions with very little effort.
Related techniques: Hijacked devices, clicks pamming, pixel stuffing, ad stacking, geomasking, and bad bots.
MSISDN injection
Example of MSISDN injection
What are MSISDN injections?
MSISDN injections aren’t always malicious -- some operators use them to enrich transactions in direct carrier billing. However, fraudsters inject fake MSISDN numbers to auto-subscribe unaware users to offers that they might not necessarily want.
How do MSISDN injections work?
MSISDN injections use sophisticated pieces of automated software that emulate the journey of the user. Infected devices declare a user-agent header not normally associated with human activity. Headers containing MSISDN information are a clear indication of fraud.
What are the threats posed by MSISDN injections?
MSISDN injections lead to subscription fraud. They are considered very malicious and are technologically difficult for fraudsters to enact. They are also associated with very localized attacks.
Related techniques: Bad bots, botnets, malware, geomasking, proxy traffic, and datacenter traffic.
Clickjacking
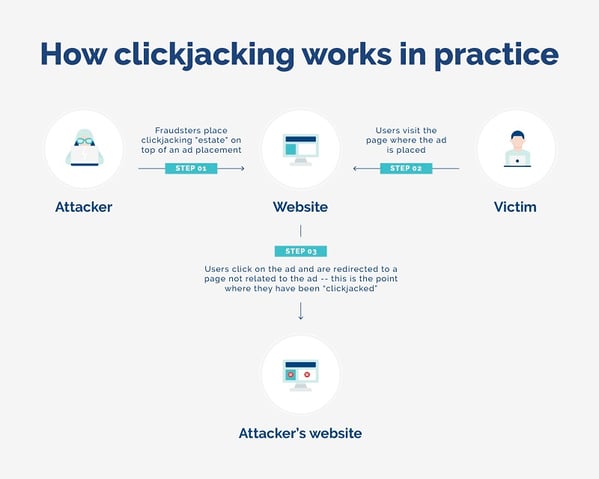
What is clickjacking?
Clickjacking occurs when users are fooled into clicking a website element that is either invisible or disguised as a different element. This ad fraud technique tricks users into downloading malware, visiting unsafe websites, giving away personal credentials, authorizing transfers of money, and activating cameras and microphones.
How does clickjacking work?
Invisible or disguised malicious links or HTML elements are placed over a website’s user interface inside an iFrame. The user believes they are clicking the visible page, but they are really clicking on the invisible or disguised element that has been placed on top of it.
What are the threats posed by clickjacking?
Clickjacking is a malicious ad fraud technique since it is a form of attribution fraud. It can also steal people’s personal information, withdraw money, and lead users to insecure web pages. It’s also a relatively easy method of ad fraud for fraudsters to deploy and is usually quite localized.
Related techniques: N/A.
iFrame traffic
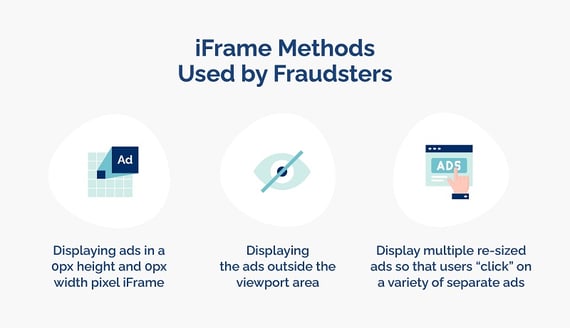
What is iFrame traffic?
iFrames are web elements that allow the insertion of external content into a webpage (e.g. a social widget or a YouTube video). iFrame traffic is the sum total of the web traffic that happens to be displayed inside one of those iFrames.
How does iFrame traffic work?
Fraudsters can use iFrames to load entire pages in a window of 0 height and 0 width. This generates false visits as the users are not able to effectively see the content of the page.
iFrames can also be loaded transparently over a web page. A fraudster could intercept a click made by a user on this top layer and use it for unintended purposes e.g. a purchase button.
What are the threats posed by iFrame traffic?
Traffic run on iFrames is not fraudulent, per se, and it’s a method that has valid use cases. However, it can pose a vulnerability when it’s used to generate false visits, or to deceive the user into clicking something they don’t intend to.
iFrame traffic can be used to carry out impression fraud, click fraud, lead fraud, subscription fraud, attribution fraud, and can lead to skewed analytics.
Related techniques: Clickjacking, ad stacking, and pixel stuffing.
Proxy traffic
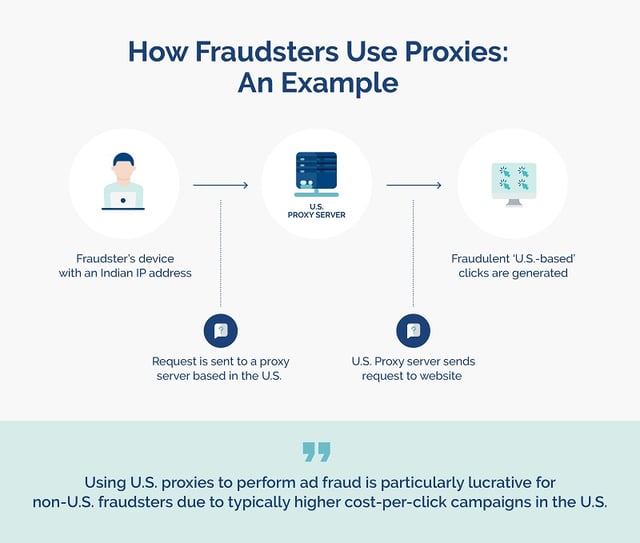
What is proxy traffic?
Proxy traffic is web traffic that has been proxied through one or more different servers.
How does proxy traffic work?
Fraudsters use proxy traffic to allow anonymous browsing by hiding the location of a user’s IP address in order to enable fraudulent activity.
This can cause advertisers to believe that their traffic is coming from high-tier countries, when in fact it’s coming from countries with lower-quality and less valuable traffic. This can result in them paying for leads they haven’t actually obtained.
What are the threats posed by proxy traffic?
Proxy traffic can be used to carry out impression fraud, click fraud, lead fraud, subscription fraud, attribution fraud, skewed analytics.
Related techniques: Bad bots, geomasking, and datacenter traffic.
Click injections
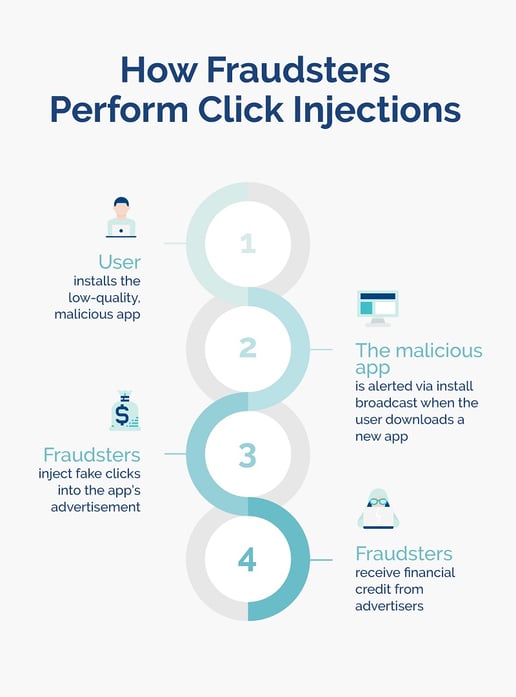
What are click injections?
Click injections are a sophisticated type of click spamming affecting Android devices. Fraudsters publish or have access to a downloaded app that listens to “install broadcasts”, which notifies them when a new app is being downloaded.
Clicks are triggered after the download is complete but before the app is opened by the user, which gives the impression that that click -- the most recent -- is the click that delivered the download. Fraudsters are then compensated for the attribution.
How do click injections work?
Fraudsters often use low-quality apps, such as apps that provide phone wallpapers, to infect devices. These apps can run in the background and appear “asleep” until the install broadcast informs it to generate clicks on a new download.
What are the threats posed by click injections?
Advertising budget loss, skewed data, and damage to advertisers’ segmentation of traffic are all threats posed by click injections. Since click injections directly infect devices, they are considered quite a malicious form of ad fraud, and are also easy to implement.
Related techniques: Malware.
Datacenter traffic
What is datacenter traffic?
Data centers are large facilities that house networked computers that centralize organizations’ IT operations, including the processing, storing, and sharing of data. Data centers are attractive to fraudsters since they can hide very well within them, and are considered as non-compliant traffic.
How does datacenter traffic work?
Data centers have networks of servers that have their own IP addresses, and often organizations will provide a proxy service to their users. Fraudsters can route the bots they use through the proxy services to avoid detection via IP addresses.
What are the threats posed by datacenter traffic?
Datacenter traffic can cause impression fraud, click fraud, lead fraud, subscription fraud, attribution fraud, and can skew data and analytics.
A lot of datacenter traffic is not malicious and is simply registered as nonhuman traffic. However, several schemes have been uncovered whereby fraudsters load ads on fabricated websites and claim the falsified ad revenue.
Related techniques: Bad bots, malware, and proxy traffic.
Click spamming
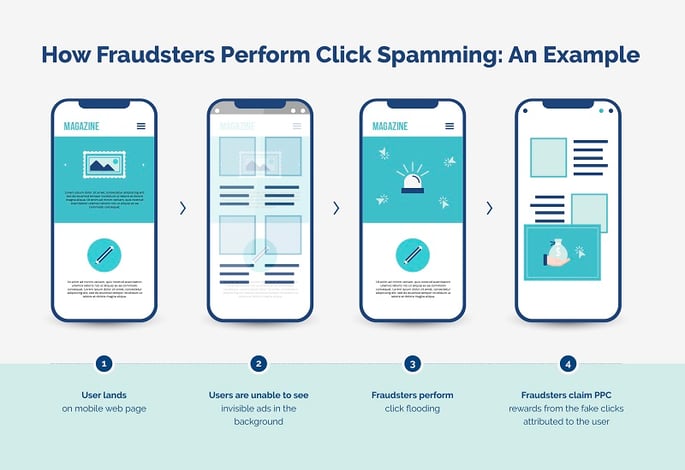
What is click spamming?
Click spamming occurs when fraudsters send a large number of low-quality fake clicks -- known as click flooding -- to an ad in an attempt to fraudulently capture PPC budgets or obtain attribution before an action (such as an app installation).
How does click spamming work?
To carry out click spamming, fraudsters need users to open a webpage operated by the fraudster or download a malicious app to their mobile device. The app or website will have an automated process coded into it, known as click bots.
Once they do this, fraudsters can:
- Send out a flurry of fake clicks, usually to invisible ads, while the app is running
- Generate impression fraud via fake clicks, while the impressions appear to be real ad engagements
- Send clicks from users’ devices to random vendors, where they can then collect the payout on ads.
These actions are carried out without the user’s knowledge or consent.
In cases of install-focused campaigns, when fraudsters are successful in obtaining the last click, they then receive attribution for the installation, including the paid commission. As a useful standard in the industry, 75% of app installs are considered “organic” if they occur within an hour of the click, and 94% are considered organic installs within 24 hours of the click. Anything outside of these parameters might be an indication of click spamming.
What are the threats posed by click spamming?
In terms of maliciousness, click spamming isn’t the worst form of ad fraud, but it does drain organizations’ budgets both quickly and easily, and deeply skews marketing data. It’s also not constricted to any geographical location and affects all types of organizations.
Related techniques: Botnets, click farms, bad bots, and data traffic.
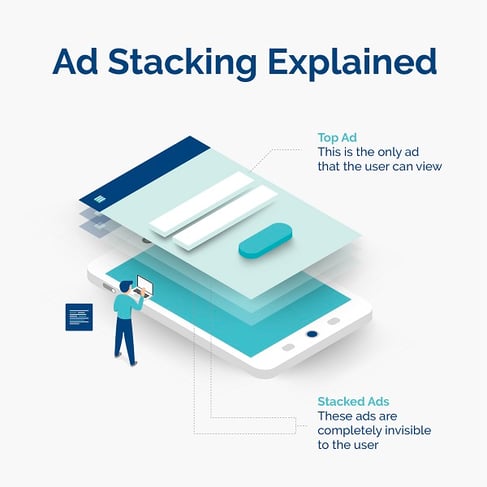
Ad stacking
What is ad stacking?
Ad stacking occurs when fraudsters stack multiple ads on top of one another in a single ad placement. The top ad is the only ad visible to the user, yet advertisers are billed for all of the false ad impressions and clicks from the ads that lay underneath.
How does ad stacking work?
A website is created and advertising space is made available. Fraudsters then join ad exchanges to sell advertising spaces. Once ad space is bought, fraudsters load multiple invisible ads on top of one another, and advertisers are charged for the fake impressions they generate.
What are the threats posed by ad stacking?
Ad stacking isn’t as nefarious as other ad fraud techniques and is moderately difficult for fraudsters to achieve. However, like many other ad fraud techniques, ad stacking drains budgets quickly, causes fake impressions, and leads to misrepresented campaign data and analytics. It is also applicable to almost all geographies and verticals.
Related techniques: Bad bots, botnets, malware, and iframe traffic.
Geomasking
What is geomasking?
Geomasking occurs when fraudsters hide the location of the leads they generate. Since ad campaigns often have different ad spends for different locations (for example, a lead might be worth more coming from the U.S. than from Brazil), fraudsters spoof IP addresses to make leads and traffic appear more valuable than they actually are. Basically, advertisers pay out for high-quality leads, in return for low-quality traffic.
How does geomasking work?
Fraudsters spoof IP addresses to hide the real identity and location of the fraudster, and to appear as an identity aligned with the ad targeting of the advertiser.
What are the threats posed by geomasking?
Geomasking practices can be used to carry out impression fraud, click fraud, lead fraud, subscription fraud, attribution fraud, and can skew data and analytics.
Campaigns that succumb to geomasking practices can see their budgets quickly drained.
Related techniques: Bad bots, botnets, malware, click spamming, click farms, datacenter traffic, and proxy traffic.
Pixel stuffing
What is pixel stuffing?
Pixel stuffing is the act of stuffing multiple ads into pixels so small that they can’t be detected by human users. Although they can’t be seen by the human eye, these illegitimate ads generate impressions by real users.
How does pixel stuffing work?
Fraudsters first build a website and join an ad exchange to deliver and display ads as a publisher. Then, they compress ads into 1x1 pixel frames on the website, and often use bad bots to create fake impressions, clicks, or leads to sell onto an ad exchange. Finally, fraudsters cash out on the profit made from fraudulent impressions.
What are the threats posed by pixel stuffing?
Although pixel stuffing isn’t a particularly malicious ad fraud technique, it does result in advertisers being charged for impressions that are never seen, skewed analytics, and missed targets. Pixel stuffing is a relatively difficult ad fraud technique to carry out, but is a method used all over the world.
Related techniques: Iframe traffic, bad bots, botnets, malware, geomasking, proxy traffic, and datacenter traffic.
Know your enemy
If you don’t know which types of ad fraud are affecting your organization, you can’t know how to best protect your organization from them.
Some organizations use manual methods to protect against the effects of several ad fraud techniques. However, manual methods are inadequate when it comes to protecting your organization. The only reliable and secure way to detect and mitigate ad fraud is to enlist the use of an anti-fraud solution.
For example, anti-fraud solution Opticks:
- Uses machine learning to identify reproduced patterns and apply algorithms to detect new bad bot patterns
- Filters traffic identified as click farm activity to prevent it from depleting your campaign budgets
- Detects fraudulent traffic by looking at existing traffic data and analyzing the behavior on ads to compare it with real-time activity -- when it detects anomalies, it can quickly and automatically prevent fraudulent traffic from affecting campaigns
Plus, while some ad fraud techniques are more widespread and common than others, organizations must be aware of the types of ad fraud that can affect their specific use case. In some instances, location can also correlate with certain types of ad fraud. In our Annual 2020 Ad Fraud Report, we breakdown the occurrence of different types of ad fraud worldwide.
To find out more about how we can work together to prevent ad fraud from destroying your ad campaigns, click here to request a free Opticks demo.